Currently, we have the version TrueNAS SCALE 22.12.2, we have tested each of the directives "server signing = required, server smb encrypt = required, smb encrypt = required, client ipc max protocol = SMB2," individually and in combination, but the "SMB Signing" vulnerability is not being fixed.
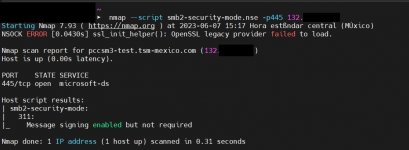
In the previous two versions, this directive "server signing = required" at the SMB service level does resolve the issue, but in this version, that directive and others do not generate any changes. When running "nmap --script smb2-security-mode.nse -p445 ip," the result is "Message signing enabled but not required."
In the previous two versions, this directive "server signing = required" at the SMB service level does resolve the issue, but in this version, that directive and others do not generate any changes. When running "nmap --script smb2-security-mode.nse -p445 ip," the result is "Message signing enabled but not required."