Snow
Patron
- Joined
- Aug 1, 2014
- Messages
- 309
Loged in to my primary NAS to see it ruining at 100%, this is not normal. I started to dig and after ruining top and ps aux in the GUI shell. I found some strange stuff going on. I've never installed or operated any cryptocurrency mining software on my Turenas.
I found some user that I did not create in top. the user was running Java as user 333. ps aux showed Crypto Returns for ever one on my 24 cpus cores. Also Some other strange stuff like a remote mouse and other stuff post in screen shots below. I also include a debug file.
Any and all advice is welcome. Do I need to go scorched earth policy on my nas? just wipe the system and disks or will a config reinstall wipe the access? I still have the problem of how they got on the system. Am I just being paranoid? Should I contact law enforcement ?
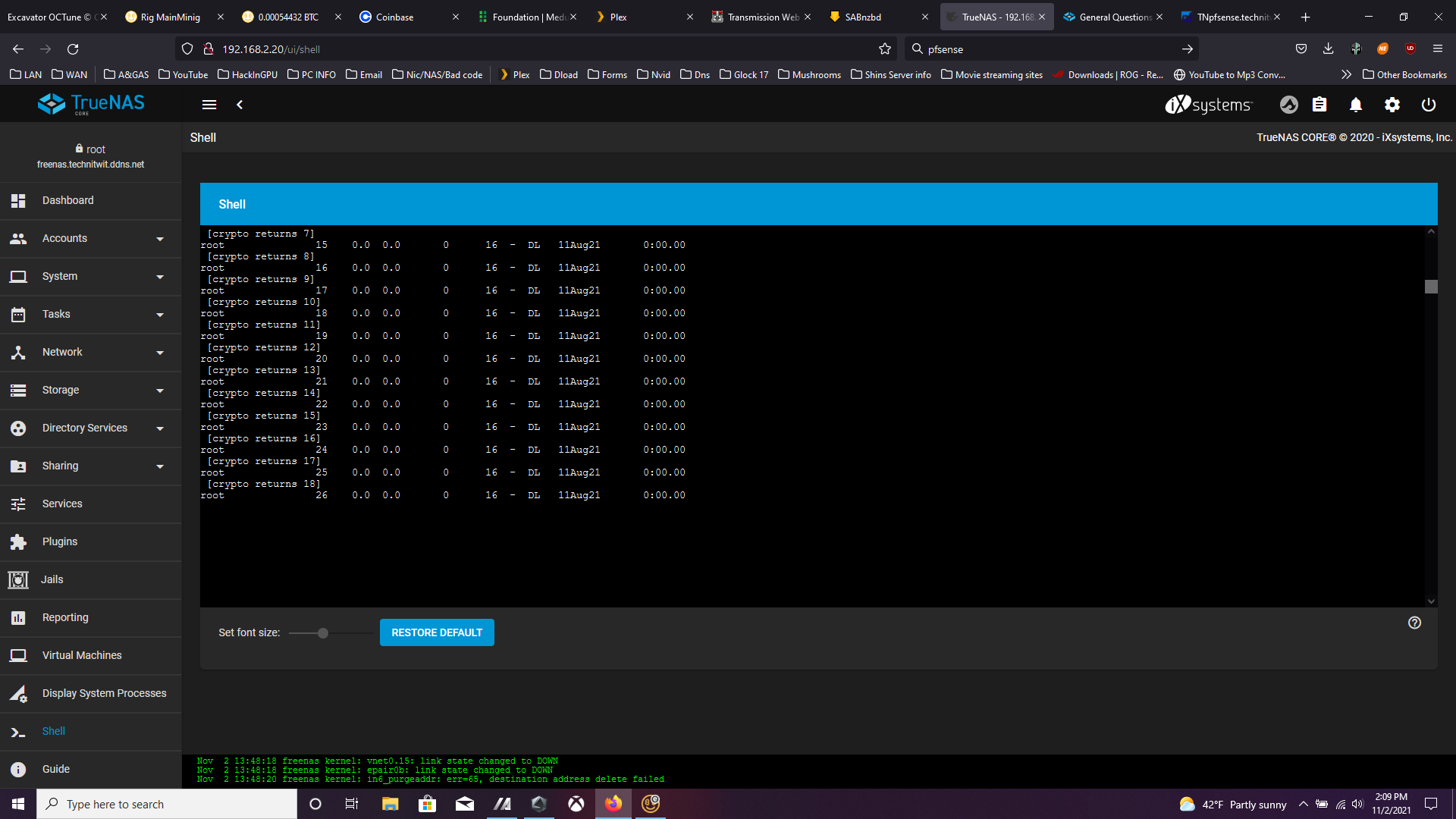



I found some user that I did not create in top. the user was running Java as user 333. ps aux showed Crypto Returns for ever one on my 24 cpus cores. Also Some other strange stuff like a remote mouse and other stuff post in screen shots below. I also include a debug file.
Any and all advice is welcome. Do I need to go scorched earth policy on my nas? just wipe the system and disks or will a config reinstall wipe the access? I still have the problem of how they got on the system. Am I just being paranoid? Should I contact law enforcement ?

